Search
Items tagged with: Cybersecurity
Hold the phone — literally, in the case of @404mediaco’s @josephcox, who hasn’t had a cellphone since around 2017 due to concerns about information security. He wrote about a privacy-focused network, previously available just to members of the military, that piqued his interest. [This story may be paywalled]
404media.co/i-dont-own-a-cellp…
#Security #InfoSec #Cellphones #Hacking #CyberSecurity #Technology #Tech #Newstodon #NewstodonFriday #FollowFriday
I Don't Own a Cellphone. Can This Privacy-Focused Network Change That?
A small tech company called Cape has been selling a privacy-focused cellphone service to the U.S. military. Now Cape will be offering its product to high-risk members of the public.Joseph Cox (404 Media)
Cybercriminals break into #AndrewTate’s online ‘university,’ steal user data and flood chats with emojis
techcrunch.com/2024/11/21/hack…
#cybersecurity #privacy #DataBreach

Hackers break into Andrew Tate's online 'university,' steal user data and flood chats with emojis | TechCrunch
Hackers have breached an online course founded by ostensible influencer and self-described misogynist Andrew Tate, leaking data on close to 800,000 users,Zack Whittaker (TechCrunch)
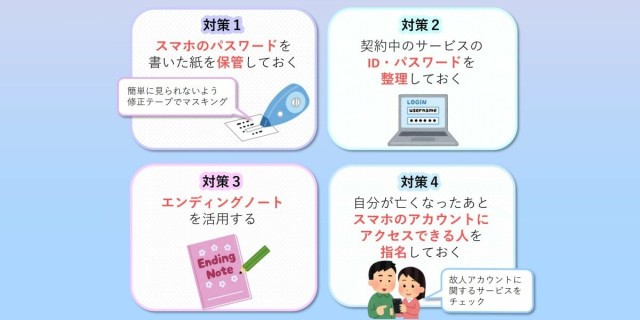
Put your usernames and passwords in your will, advises Japan's government
Digital end of life planning saves your loved ones from a little extra anguishSimon Sharwood (The Register)
#Google's AI tool, OSS-Fuzz, has detected 26 #vulnerabilities in #opensource projects, including a significant flaw in #OpenSSL.
This flaw, which could lead to application crashes or remote code execution, has existed for nearly 20 years and was only found thanks to AI-generated testing methods.
#infosec #cybersecurity #tech #AI #genAI
Have you heard about the latest losers? theregister.com/2024/11/20/dli…
#dlink #cybersecurity #Router #vpn #internet #Software #Firmware #fail #bug #economy #Problem #security #news

D-Link tells users to trash old VPN routers over bug too dangerous to identify
Vendor offers 20% discount on new model, but not patchesConnor Jones (The Register)
Hello kind readers!
I'm in desperate need of a job and need your help connecting with hiring managers. I'm looking for the following (or related) roles:
1. technical program manager
2. security engineer/analyst
3. network security engineer/analyst
4. privacy engineer/analyst
5. SOC/NOC engineer/analyst
6. data center technician manager/engineer
CV: https://[yawnbox.is]/docs/cv-priv.pdf
I live in The Hague (NL) and i'm from Seattle (WA, USA). Remote jobs will allow my partner and I to continue to exist in NL. Freelance jobs in NL are also great. I would need work visa sponsorship anywhere outside of USA. I would relocate anywhere for a great job.
Things are desperate for us. Please help.
📣 EMERGENCY UPDATES 📣
Apple pushed updates for 2 new zero-days that may have been actively exploited.
🐛 CVE-2024-44308 (JavaScriptCore),
🐛 CVE-2024-44309 (WebKit):
- iOS and iPadOS 17.7.2
- iOS and iPadOS 18.1.1
- macOS Sequoia 15.1.1
#apple #cybersecurity #infosec #security #ios
Interboro School District in PA was added to #RansomHub leak site today with a few screencaps as POC. The screencaps are internal files and what appear to be two employee-related pieces of personal information. There is nothing on Interboro's website about any #databreach at this time.
Sometime ago somebody shared a screenshot of a service with a cookie message along the lines of:
"We take your privacy seriously" while there also was a list of 600+ vendors with whom data would be shared. Does anyone have this screenshot & the source? I think this was by Microsoft MS365?
#Privacy #Cookies #Tech #TechPolicy #OpenSource #Data #GDPR #bigtech #Security #CyberSecurity
#China Connected #SaltTyphoon Compromised AT&T / #Verizon / #LawfulIntercept #Backdoors
Installed #Windows Kernel Rootkit
"backdoors protect kids"....
Don't buy into this #propaganda.
#privacy #News #infosec #cybersecurity #USA #Telecom #CISA #ATT
heise.de/en/news/China-s-cyber…

China's cyber spies intercept phone data and calls from US network operators
Chinese cyber spies infiltrated US network operators. Conversations and data from government and politicians were intercepted, as were police wiretaps.Frank Schräer (heise online)
China's cyber spies intercept phone data and calls from US network operators
Chinese cyber spies infiltrated US network operators. Conversations and data from government and politicians were intercepted, as were police wiretaps.
heise.de/en/news/China-s-cyber…
#ATT #Cybersecurity #Cyberspionage #DonaldTrump #FBI #Provider #Security #Spionage #Verizon #news
El Dorado Union High School District in California notified the Maine AG's office of a breach that occurred between May 25 and June 18. It affected 31,896 people and involved names and SSN:
maine.gov/agviewer/content/ag/…
#HowTo Selfhosting Nearly Any Site On The Darkweb Using I2PD (light option ideal for single board computers and more
SECURITY BENEFIT: end-to-end #encryption overlay (no #https needed) & w/network range/IP not viewable, more challenge to attack other server services
READ / WATCH ON I2P: righttoprivacy.i2p/selfhost-da…
#i2pd #darknet #darkweb #development #webDev #encryption #infosec #cybersecurity
tube.tchncs.de/w/brDxfhZNeMDbj…

Selfhosting Darknet Websites Using I2PD
HOWTO: Selfhost Nearly ANY Website On The Darkweb - Easier Than You Think! We begin by installing NGINX webserver, for self-hosting our website code, and gain the added benefit of end-to-end encry...tchncs
Pregnancy Tracking #App ‘What to Expect’ Refuses to Fix Issue that Allows Full Account Takeover
What to Expect is a popular pregnancy tracking app available for #ios and #android.
An exposed API endpoint handling password reset requests for the app does not require authentication or enforce rate limits and is vulnerable to brute force attacks.
#privacy #security #cybersecurity
404media.co/pregnancy-tracking…
Pregnancy Tracking App ‘What to Expect’ Refuses to Fix Issue that Allows Full Account Takeover
Vulnerabilities in the popular What to Expect app include one that allows a full account take over, and another that exposes that email address of forum admins.Joseph Cox (404 Media)
Idaho man who hacked medical entities and made vile threats sentenced to 10 years in prison:
databreaches.net/2024/11/13/id…
This is a case that started because the threat actor, "Lifelock," contacted DataBreaches to try to get DataBreaches.net to report on victims who hadn't paid his ransom demands.
Some of his court filings tried to blame me for the FBI raiding him and seizing his devices. The FBI did their own investigation but yes, it was my reporting that initially made the FBI aware of Lifelock (real name Robert Purbeck).
Get ready for the transition to @thunderbird mobile!
blog.iode.tech/get-ready-for-t…
#thunderbird #android #rom #privacy #cybersecurity #adblocker #iodé #degoogle #opensource
#Amazon confirms #employee data stolen after #hacker claims #MOVEit #breach
source: techcrunch.com/2024/11/11/amaz…
“Amazon and AWS systems remain secure, and we have not experienced a #security event. We were notified about a security event at one of our property management vendors that impacted several of its customers including Amazon. The only Amazon information involved was employee work contact information, for example work email addresses, desk phone numbers, and building locations,” Montgomery said.
If not even a company like Amazon can store its data securely, is there any security at all? Amazon doesn't lack money or experts, but it does seem to lack secure software.
#fail #cybersecurity #problem #software #internet #news #economy #hack #cloud

Amazon confirms employee data stolen after hacker claims MOVEit breach | TechCrunch
Amazon has confirmed that employee data was compromised after a “security event” at a third-party vendor. In a statement given to TechCrunch on Monday,Carly Page (TechCrunch)
bleepingcomputer.com/news/secu…
Suspected #Snowflake #Hacker Arrested in #Canada
source: 404media.co/suspected-snowflak…
For more than a week #Judische, the hacker linked to the #AT&T, #Ticketmaster and other breaches, has not been responding to messages. That's because he's been arrested.
#police #jail #cybercrime #cybersecurity #hack #news
Suspected Snowflake Hacker Arrested in Canada
For more than a week Judische, the hacker linked to the AT&T, Ticketmaster and other breaches, has not been responding to messages. That's because he's been arrested.Joseph Cox (404 Media)
Wild ass day in the Tor node operator world. Got an email from my VPS, forwarding a complaint from WatchDog CyberSecurity saying that my box was scanning SSH ports!
> Oh no, oh no, I knew I should have set up fail2ban, oh god why was I so lackadaisical!
So I remote in to the machine: no unusual network activity, no unusual processes, users, logins, command history, no sign that anything is doing anything I didn't tell it to do.
So what's up? Turns out there's been a widespread campaign where some actor is spoofing IPs to make it look like systems running Tor are scanning port 22: forum.torproject.org/t/tor-rel…
Operators from all over are saying they're getting nastygrams from their VPS providers because WatchDog is fingering their source IPs (which are being spoofed and NOT part of a global portscanning botnet).
@delroth did an amazing writeup of the whole thing here: delroth.net/posts/spoofed-mass…
#tor #infosec #cybersecurity #threatintel #privacy
![[tor-relays] Tor relays source IPs spoofed to mass-scan port 22?](https://friendica.hellquist.eu/photo/preview/640/3344604)
[tor-relays] Tor relays source IPs spoofed to mass-scan port 22?
It would be hard to explain to Verizon I run Tor relays since they technically don't allow servers. I hope I'm not forced onto AT&T Internet Air as my particular co-op rental unit won't let met get Spectrum even when other units can, not that I wante…Tor Project Forum
Hundreds of #code #libraries posted to #NPM try to #install #malware on dev machines
source: arstechnica.com/security/2024/…
The malicious packages have names that are similar to legitimate ones for the Puppeteer and Bignum.js code libraries and for various libraries for working with #cryptocurrency.
Dependency hell 👎👿
#software #problem #development #library #dependency #security #cybersecurity #news #cybercrime #attack

Hundreds of code libraries posted to NPM try to install malware on dev machines
These are not the the developer tools you think they are.Dan Goodin (Ars Technica)
#Mudita Kompakt: A minimalist E Ink® #phone for more life, less screen time, and fewer distractions. Essential features with clear UI and #privacy focus.
Source: kickstarter.com/projects/mudit…
No #Google apps onboard 👍
#news #smartphone #android #mobile #technology #cybersecurity
🚀 Staff Security Engineer, Vulnerability Management
🏢 Coinbase
📍 Multiple remote locations
🔗 Apply now: totalcyber.io/jobs/coinbase/st…
#cyber #cybersecurity #job #mastodon #fediverse #fedihire #fedijobs #getfedhired #infosec #hiring #gethired #joboffer #flossjobs #jobhunt
Have you heard that social engineering is the new hotness in #cybersecurity ? You can have great defenses but if you allow your users to be tricked into using a threat actor’s Remote Monitoring and Management (RMM) tool badness will happen. Examples of #RMM tools include ScreenConnect and AnyDesk. I highly recommend reviewing this list and proactively blocking the tools not used by your organization
#cybersecurity #cysec #insiders #infosec
cybersecurity-insiders.com/med…

Medusa Ransomware attack impacts 1.8 million patients - Cybersecurity Insiders
AI is evolving at a rapid pace, and the uptake of Generative AI (GenAI) is revolutionising the way humans interact and leverage this technology. GenAI isNaveen Goud (Cybersecurity Insiders)
🚀 Comcast Cybersecurity: Penetration Tester 3
🏢 Comcast
📍 Philadelphia, United States
🔗 Apply now: totalcyber.io/jobs/comcast/com…
#cyber #cybersecurity #job #mastodon #fediverse #fedihire #fedijobs #getfedhired #infosec #hiring #gethired #joboffer #flossjobs #jobhunt
🚀 Cybersecurity Engineering Manager
🏢 RTX Corporation
📍 Lane Cove West, Australia
🔗 Apply now: totalcyber.io/jobs/rtx-corpora…
#cyber #cybersecurity #job #mastodon #fediverse #fedihire #fedijobs #getfedhired #infosec #hiring #gethired #joboffer #flossjobs #jobhunt

Threat actors are stepping up their tactics to bypass email protections - Help Net Security
Most organizations use emails with built-in security features but cybercriminals often find ways to bypass these protections.Help Net Security
Join #BSidesPhilly on Dec 6th at LIVE! Casino and Hotel to hear this and all of our exciting talks!
Click the link to grab your tickets today! buff.ly/47onQwU
Early Bird sale! All tickets $50 until November 16th. Regularly priced tickets $65.
BSides Philly 2024
December 6th, 8 AM - 6 PM LIVE! Hotel & Casino, 900 Packer Avenue, Philadelphia, PA 19148 Join us for an exhilarating day of cutting-edge cybersecurity discussions and networking at BSides Philly! Our exclusive event will bring together industry ex…TicketLeap
Fraudsters Exploit US General Election Fever, FBI Warns.
Read more in my article on the Tripwire blog: tripwire.com/state-of-security…
#cybersecurity #scam #politics #election

Fraudsters Exploit US General Election Fever, FBI Warns
The FBI warns of election scams targeting voters with fake donations, merchandise, and voter registration links. Stay vigilant!www.tripwire.com
🚀 Senior Risk Governance Manager - CIO
🏢 Aviva
📍 Multiple locations
🔗 Apply now: totalcyber.io/jobs/aviva/senio…
#cyber #cybersecurity #job #mastodon #fediverse #fedihire #fedijobs #getfedhired #infosec #hiring #gethired #joboffer #flossjobs #jobhunt
#Matrix 2.0 Is Here!
matrix.org/blog/2024/10/29/mat…
#FOSS #privacy #cybersecurity #decentralization

Matrix 2.0 Is Here!
Matrix, the open protocol for secure decentralised communicationsMatthew Hodgson (matrix.org)
“It’s no longer just identifying a best-in-class solution or something off the shelf that is technically feasible and affordable - now the cybersecurity professional needs to understand what the implications of that are and needs to be able to reasonably assert back to the business." - Casey Marks, Chief Qualifications Officer at ISC2.
As more organizations adopt services, they're also opening a new attack vector. In this feature for The Inference, I examine how cloud #cybersecurity professionals are working to keep us safe - and the skills they require. (Spoiler: It isn't all technical skills)
darktrace.com/the-inference/th…

The rising importance of cloud security specialists in cyber defense | The Inference
As organizations adopt cloud services, they're also opening a new attack vector. Here's how cloud security professionals are working to keep us safe.Darktrace
Never ending story about the #security of fitness app...
Source: thehindu.com/sci-tech/technolo…
#news #stava #cybersecurity #sports #Problem #Software #privacy #politics #fail #online #cloude #surveillance #bigdata #economy

Fitness app Strava gives away location of Biden, Trump and other leaders, French newspaper says
Le Monde reported that movements of some of the world’s most powerful leaders could be tracked online through a fitness app used by their bodyguards.The Hindu
CCCS (Canada): Statement on People's Republic of China reconnaissance of Canadian systems
This got overlooked Friday: The Canadian Centre for Cyber Security (CCCS) warned Canadian organizations to harden their networks against reconnaissance scanning, performed by a Chinese state-sponsored threat actor over several months. Targets were multiple organizations across multiple sectors including:
- Government of Canada departments and agencies
- federal political parties
- the House of Commons and Senate
- democratic institutions
- critical infrastructure
- defense sector
- media organizations
- think tanks
- Non Governmental Organizations (NGOs)
h/t: @campuscodi
#china #cyberespionage #canada #cccs #threatintel #infosec #cybersecurity #cyberthreatintelligence #CTI
Now live: the discussion I had with Chris Hughes and @caseyjohnellis on systemic issues in #cybersecurity:
resilientcyber.io/p/resilient-…
In which I pulled a “Legally Blonde” on Casey; see if you can catch it 😉

Resilient Cyber w/ Wendy Nather & Casey Ellis - Systemic Cyber Struggles
In this episode of Resilient Cyber Chris Hughes chats with Cyber industry veterans and long-time leaders Wendy Nather and Casey Ellis about systemic cyber struggles, issues that still plague us over the years, and some of the economic incentives at p…Chris Hughes (Resilient Cyber)