Search
Items tagged with: cybersecurity
🐛 NEW SECURITY CONTENT 🐛
💻 macOS Tahoe 26.3 - 57 bugs fixed
support.apple.com/en-us/126348
💻 macOS Sonoma 14.8.4 - 42 bugs fixed
support.apple.com/en-us/126350
📱 iOS and iPadOS 26.3 - 41 bugs fixed
support.apple.com/en-us/126346
📱 iOS and iPadOS 18.7.5 - 37 bugs fixed
support.apple.com/en-us/126347
💻 macOS Sequoia 15.7.4 - 36 bugs fixed
support.apple.com/en-us/126349
🥽 visionOS 26.3 - 29 bugs fixed
support.apple.com/en-us/126353
⌚ watchOS 26.3 - 18 bugs fixed
support.apple.com/en-us/126352
📺 tvOS 26.3 - 16 bugs fixed
support.apple.com/en-us/126351
#apple #cybersecurity #infosec #security #ios
About the security content of iOS 26.3 and iPadOS 26.3 - Apple Support
This document describes the security content of iOS 26.3 and iPadOS 26.3.Apple Support
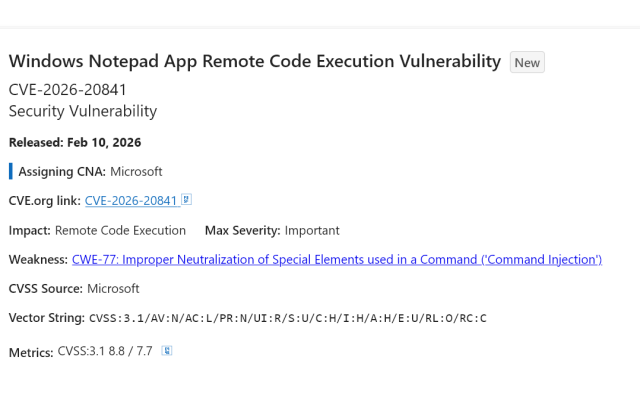
They finally did it. Microsoft has successfully over-engineered a text editor into a threat vector.
This CVE is an 8.8 severity RCE in Notepad of all things lmao.
Apparently, the "innovation" of adding markdown support came with the ability of launching unverified protocols that load and execute remote files.
We have reached a point where the simple act of opening a .md file in a native utility can compromise your system. Is nothing safe anymore? 😭
msrc.microsoft.com/update-guid…
#noai #microslop #microsoft #windows #programming #writing #windows11 #enshittification #cybersecurity #infosec #technology
France Just Created Its Own Open Source Alternative to Microsoft Teams and Zoom
Not only for them, but any other non-European videoconferencing software.Sourav Rudra (It's FOSS)
🚨 A WhatsApp bug lets malicious media files spread through group chats
「 The bug affects WhatsApp on Android and involves zero‑click media downloads in group chats. You can be attacked simply by being added to a group and having a malicious file sent to you 」
malwarebytes.com/blog/news/202…
#whatsapp #malware #cybersecurity

A WhatsApp bug lets malicious media files spread through group chats | Malwarebytes
Google’s Project Zero team found that WhatsApp can download a malicious media file without you doing anything at all.Pieter Arntz (Malwarebytes)
RE: infosec.exchange/@spamhaus/116…
Folks: block the .ru TLD any and all ways that you can. #cybersecurity

The Spamhaus Project (@spamhaus@infosec.exchange)
Attached: 1 image .ru serious? 🇷🇺 ccTLD .ru had an unbelievable +3741% ⏫ in #botnet C&C domains, placing it #1 for the most abused ccTLD in the latter half of 2025.The Spamhaus Project (Infosec Exchange)
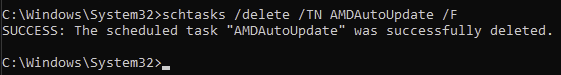
You can do the following to remove the scheduled task that executes the vulnerable AMDAutoUpdate:
1. Run cmd.exe as administrator
2. schtasks /delete /TN AMDAutoUpdate /F
This prevents the AMDAutoUpdate from executing.
Apparently AMD's AutoUpdate downloads the updates over HTTP and executes them without any validation (presumably as SYSTEM user). AMD was notified of the vulnerability but according to them "attack requiring physical access to victim's computer/device, man in the middle or compromised user accounts" are out of scope.
Madness.
source: web.archive.org/web/2026020615…
#vulnerability #infosec #cybersecurity
The RCE that AMD won't fix!
After reporting a RCE in AMD's auto-update software, they decided to not patch it due to it requiring a man-in-the-middle attack to perform.web.archive.org
Hackers exploit critical #ReactNative #Metro bug to breach dev systems
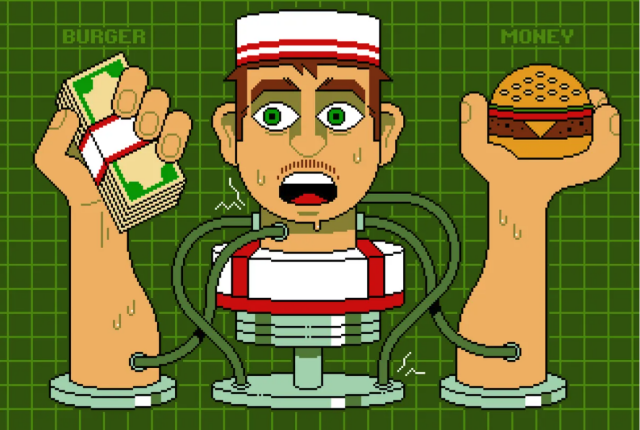
Why do LLMs fall for prompt injection attacks that wouldn’t fool a fast-food worker?
In this piece, Fastly Distinguished Engineer Barath Raghavan and security expert Bruce Schneier explain how AI flattens context—and why that makes autonomous AI agents especially risky.
A sharp, practical take on AI security. 🍔🤖: spectrum.ieee.org/prompt-injec…
#AISecurity #PromptInjection #LLMs #Cybersecurity
Why AI Keeps Falling for Prompt Injection Attacks
Why AI falls for scams that wouldn't trick a fast-food worker—and what that reveals about AI security.Bruce Schneier (IEEE Spectrum)
Signal President Meredith Whittaker warns AI agents embedded in OSes are eroding end-to-end encryption's real-world security, despite its mathematical soundness. With root-like access to messages & data, they bypass E2EE isolation—urgent rethink needed! 🔒🤖❌
cyberinsider.com/signal-presid…
#AI #Privacy #Cybersecurity #Newz #Signal

Signal president warns AI agents are making encryption irrelevant
Signal president Meredith Whittaker said AI agents embedded within operating systems are eroding the practical security guarantees of E2EE.Alex Lekander (CyberInsider)
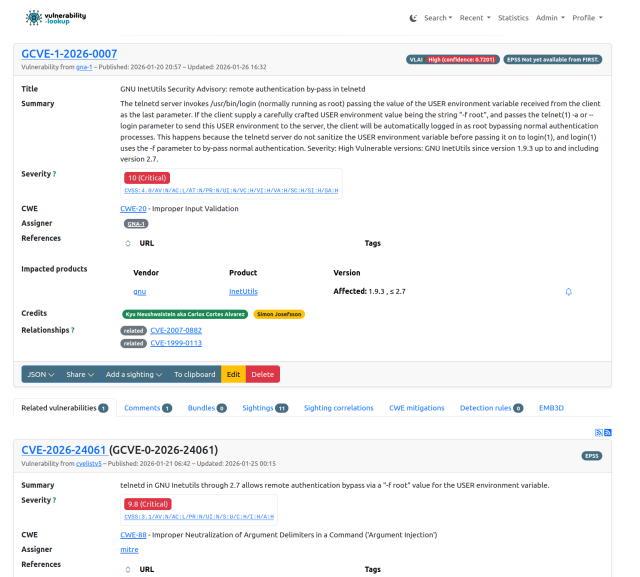
GNU InetUtils telnetd Authentication Bypass Exploited in the Wild
A critical authentication bypass in GNU InetUtils telnetd (CVE-2026-24061) is actively exploited only days after the public reporting of the flaw. It's urgent that you block any telnet server you are using from the Internet.
**THIS IS URGENT! Check if you are using Telnet anywhere in your network. IMMEDIATELY isolate the Telnet interface to trusted networks and patch the code. Then stop using Telnet and switch to SSH.**
#cybersecurity #infosec #attack #activeexploit
beyondmachines.net/event_detai…
With the extension of the CVE record format in GCVE, we added the related vulnerabilities for the "recent" telnetd. Very nifty for analyst. The edit functionality in vulnerability-lookup supports the BCP-05 extensions including relationships.
Thanks to @claudex for digging
#gcve #vulnerability #vulnerabilityManagement #cve #telnet #cybersecurity
🔗 vulnerability.circl.lu/vuln/gc…
@gcve
GCVE-1-2026-0007 - Vulnerability-Lookup
Details of the vulnerability GCVE-1-2026-0007 from gna-1 on Vulnerability-Lookup.vulnerability.circl.lu
🇫🇷 France is replacing Microsoft Teams & Zoom with its own sovereign video‑conferencing platform, Visio, in public administration by 2027.
Aims to boost digital sovereignty, keep gov data in France, and reduce reliance on US tech. Developed by DINUM, Visio is 100% French‑made.
👉 heise.de/en/news/France-replac…
#France #DigitalSovereignty #Visio #TechNews #CyberSecurity #Newz
France replaces MS Teams and Zoom with its own video conferencing software
With Visio, France is introducing its open-source video conferencing for authorities. By 2027, 200,000 civil servants are to work independently of US providers.Moritz Förster (heise online)
Either lock it down completely, or give the keys to the regime you're doing business with, but don't leave a backdoor for any opportunist on the planet to walk through.
Get it together.
thehackernews.com/2021/05/how-…
#privacy #cyberSecurity #authoritarianism

How Apple Gave Chinese Government Access to iCloud Data and Censored Apps
New Report Explains How Apple Gave Chinese Government Access to iCloud Data and Censors AppsThe Hacker News
RE: mastodon.social/@Tutanota/1159…
Super grateful to @Tutanota for sharing our experience of trying to bring digital rights advocacy to a local level!
Tuta Mail has been the secure, reliable foundation from which we could build this group! Important that we started on the right foot.
#Tuta #Florida #Privacy #Cybersecurity #DigitalRights #Tech #Miami
🏴☠️ all your OpenCodes belong to us
「 The mental model we’ve grown accustom to (with thanks to GitHub) is “copilot”, a helpful assistant with the same motivations and goals as you. The reality is closer to “untrusted contractor with root access to your entire work life.” You wouldn’t give a random freelancer root AWS keys on day one (if ever), but we hand that to AI agents without a second thought 」