Search
Items tagged with: Security
Fake AI Chrome extensions with 300K users steal credentials, emails
A malicious campaign of 30 Chrome extensions masquerading as AI assistants has infected over 300,000 users, stealing credentials, email content, and browsing data1. The extensions, dubbed "AiFrame" by LayerX researchers, share common infrastructure under the domain tapnetic[.]pro and use iframes to load remote content rather than implementing actual AI functionality1.
Popular malicious extensions still available on the Chrome Web Store include:
- AI Sidebar (70,000 users)
- AI Assistant (60,000 users)
- ChatGPT Translate (30,000 users)
- AI GPT (20,000 users)
The extensions specifically target Gmail data through content scripts that extract email content, drafts, and thread text. They can also capture voice recordings using Web Speech API and transmit data to remote servers controlled by the operators1.
Wenn Tech zur Religion wird: Warum gute Prinzipien ohne Kontext zu Dogmen werden – und wie Orientierung und realistische Schritte mehr Menschen mitnehmen. 👇
kuketz-blog.de/das-toleranzpro…
#datenschutz #opensource #tech #privacy #fedilz #sicherheit #security
🐛 NEW SECURITY CONTENT 🐛
💻 macOS Tahoe 26.3 - 57 bugs fixed
support.apple.com/en-us/126348
💻 macOS Sonoma 14.8.4 - 42 bugs fixed
support.apple.com/en-us/126350
📱 iOS and iPadOS 26.3 - 41 bugs fixed
support.apple.com/en-us/126346
📱 iOS and iPadOS 18.7.5 - 37 bugs fixed
support.apple.com/en-us/126347
💻 macOS Sequoia 15.7.4 - 36 bugs fixed
support.apple.com/en-us/126349
🥽 visionOS 26.3 - 29 bugs fixed
support.apple.com/en-us/126353
⌚ watchOS 26.3 - 18 bugs fixed
support.apple.com/en-us/126352
📺 tvOS 26.3 - 16 bugs fixed
support.apple.com/en-us/126351
#apple #cybersecurity #infosec #security #ios
About the security content of iOS 26.3 and iPadOS 26.3 - Apple Support
This document describes the security content of iOS 26.3 and iPadOS 26.3.Apple Support
"Switzerland’s military has terminated its contract with Palantir… following a security audit… concluded that U.S. intelligence agencies could potentially access sensitive Swiss defense data… significant reputational warning for the data analytics firm"
France launches "LaSuite," an open-source office suite for digital sovereignty, reducing reliance on foreign proprietary software. 🖥️
Built on Matrix/TChap, LiveKit/Visio, Grist, and Drive—all MIT-licensed for any organization to deploy. 🇪🇺
🔗 sinologic.net/en/2026-01/franc…
#TechNews #OpenSource #France #French #DigitalSovereignty #FOSS #Matrix #Privacy #EU #Security #Software #Linux #SelfHost #Government #Europe #Data #IT #PublicSector #Microsoft #Office #Tech #Cloud #LibreOffice
France chooses Open Source to secure European Sovereignty.
According to many European media outlets, the French government has just announced its commitment to a businesElio Rojano (Sinologic)
Fake 7-Zip downloads are turning home PCs into proxy nodes

Fake 7-Zip downloads are turning home PCs into proxy nodes | Malwarebytes
A convincing lookalike of the popular 7-Zip archiver site has been silently turning victims’ machines into residential proxy nodes.Stefan Dasic (Malwarebytes)
France Just Created Its Own Open Source Alternative to Microsoft Teams and Zoom
Not only for them, but any other non-European videoconferencing software.Sourav Rudra (It's FOSS)
The Shadow Campaigns: Uncovering Global Espionage

Global Espionage: Lazarus Group Targets OSS Ecosystems
North Korea's Lazarus Group is attacking developers via open source. Sonatype found over 200 malicious packages. Are you affected? Read the blog post.Sonatype Security Research Team (Sonatype)
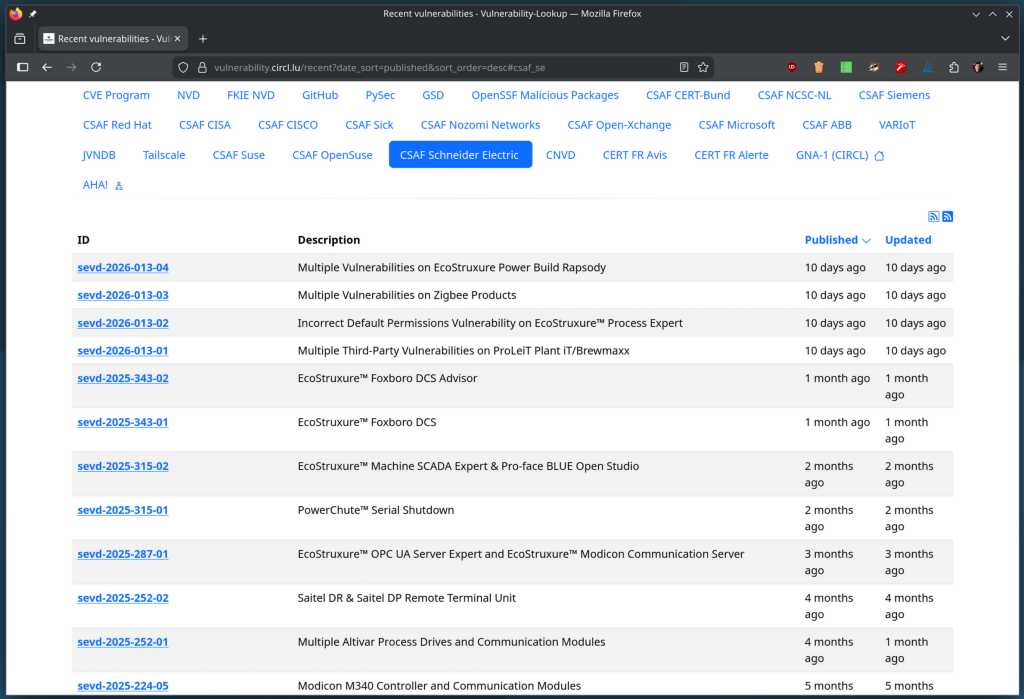
Vulnerability-Lookup 3.0.0
Fix CVSS 4.0 parsing crash in web filters
Problem Recent CVEs include CVSS 4.0 vectors (e.g. CVSS:4.0/...). The current Jinja filters rely on schema-specific version labels (cvssV3_1, cvssV4_0) which do not match extracted metrics ("3.1", ...thaicn1712 (GitHub)
Notepad++'s update servers have been compromised by Chinese hackers and all users had been exposed to malware. The developer estimated the overall compromise period spanned from June through December 2, 2025.
Users should update to version 8.9.1 (or superior) immediately.
Source: notepad-plus-plus.org/news/hij…
#security #vulnerability #windows #text #editor #notepad #foss #freesoftware #software
If you use Notepad++ update it now.
Notepad++ Hijacked by State-Sponsored Hackers
notepad-plus-plus.org/news/hij…
#tech #technology #news #technews #security #privacy #hack #china
Minimal CVE Hardened container image collection
GitHub - rtvkiz/minimal: Minimal CVE Hardened container image collection
Minimal CVE Hardened container image collection. Contribute to rtvkiz/minimal development by creating an account on GitHub.GitHub
Self-Host Weekly (30 January 2026)
#AI tags (and the #lobster everyone is going crazy over), software updates and launches, a spotlight on #VanillaCookbook - a simple #recipe platform, and more in this week's #selfhosted recap!
#selfhost #selfhosting #newsletter #foss #opensource #fosdem #homelab #privacy #security #sysadmin #devops #smarthome #fediverse #clawdbot #moltbot #openclaw #immich

Self-Host Weekly (30 January 2026)
Lobster-themed AI assistants, milestone releases, and the latest NAS operating system launchEthan Sholly (selfh.st)
Phishing attack: Numerous journalists targeted in attack via Signal Messenger

Phishing attack: Numerous journalists targeted in attack via Signal Messenger
In a phishing attack, unknown actors are apparently attempting to gain access to accounts of journalists and activists on the Signal messaging service. We explain how the attack works and how you can protect yourself against it.netzpolitik.org
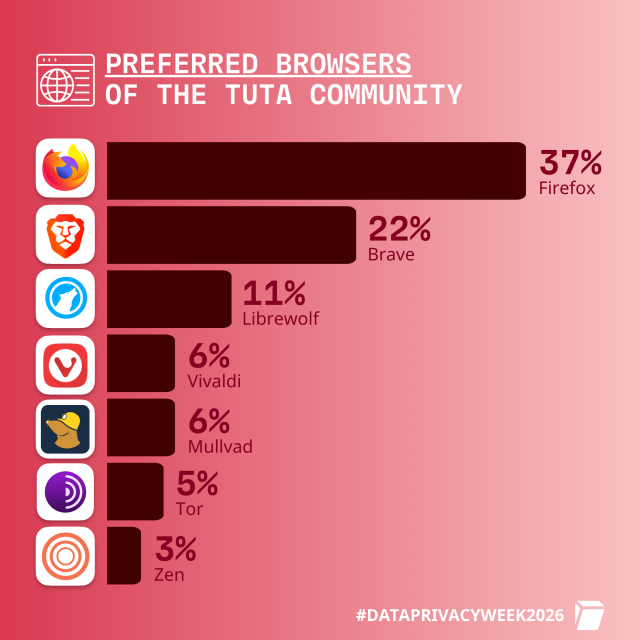
On the run up of #DataPrivacyDay we've asked the Tuta Community about your preferred Google alternatives.
Here's what you said about your favorite browsers! 🎉
golem.de/news/datenschutzdebat…
#USA #Security #Drittland #Datenschutz
If you use #GMAIL, you should be aware that as of this post's timestamp, their spam detection is down and it is likely your emails aren't being scanned for spam, unverified senders, or harmful software.
"We are aware that some Gmail users are experiencing misclassification of emails in their inbox and additional spam warnings. We are actively working to resolve the issue. As always, we encourage users to follow standard best practices when engaging with messages from unknown senders."
"We advise the users to be extra diligent in lieu of missing spam checks." #Spam #Google #InfoSec #Security #Phishing
Google Status:
google.com/appsstatus/dashboar…
Here’s what The Counteroffensive is reading today:
Putin offered to give $1 billion to #Trump’s Board of Peace from the $5 billion Russian frozen assets in the U.S, at a Russia’s #Security Council meeting.
The rest of the funds will be put to Ukraine’s post-war reconstruction.
bloomberg.com/news/articles/20…
#news #ukraine #trump #russia
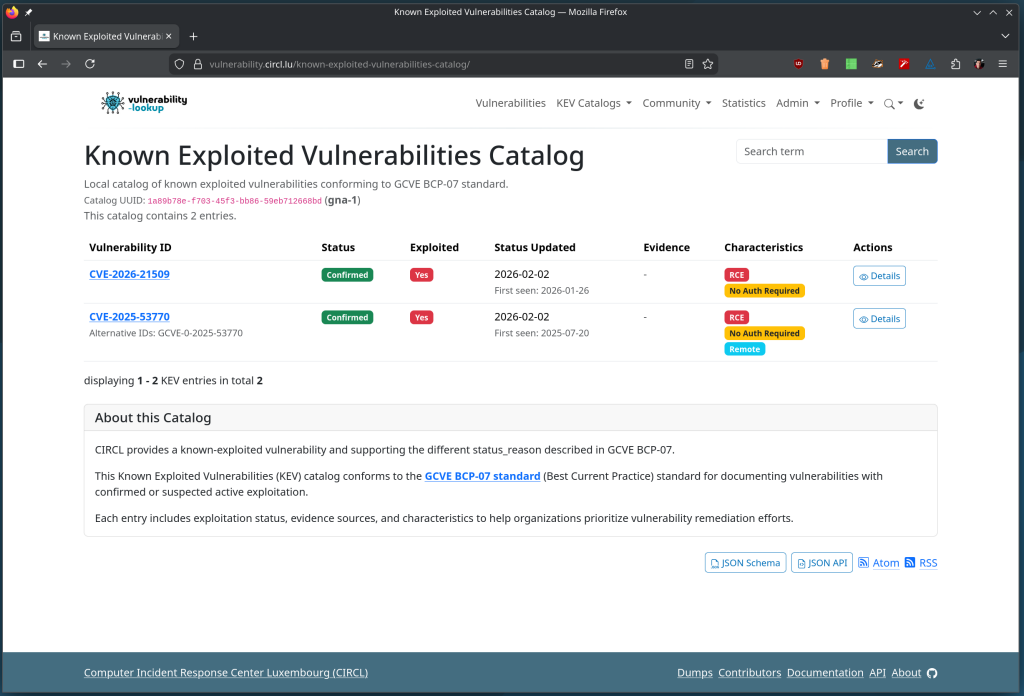
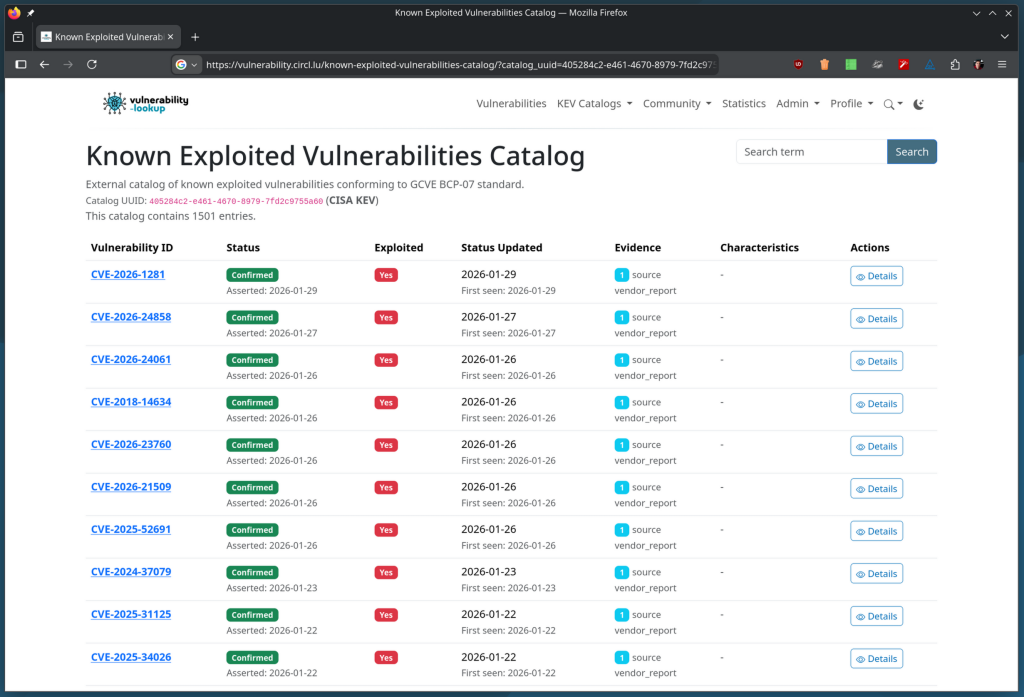
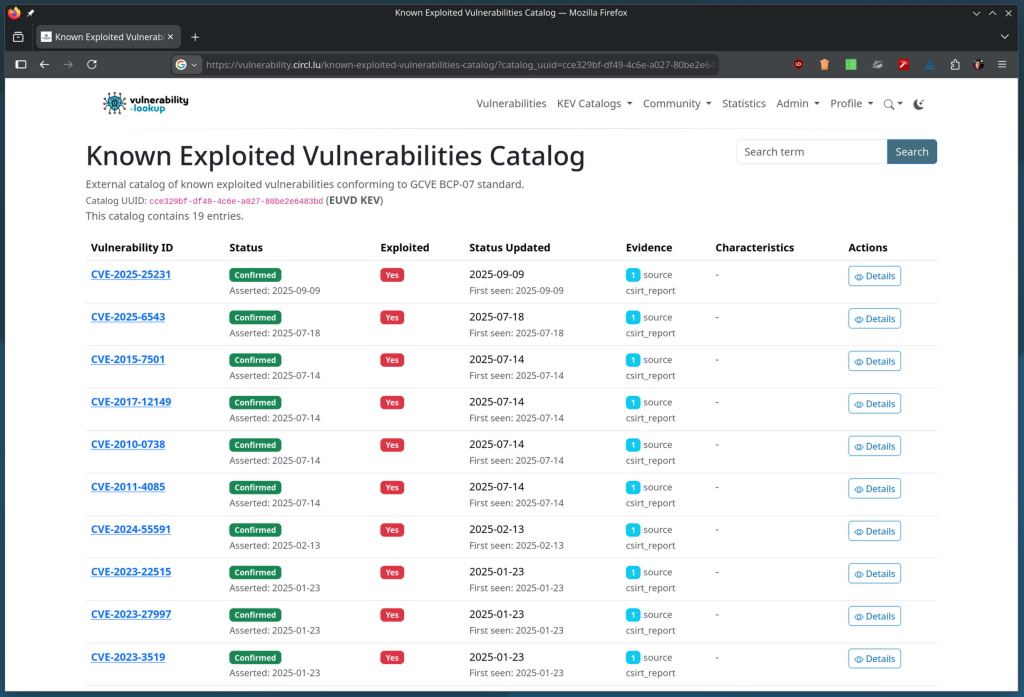
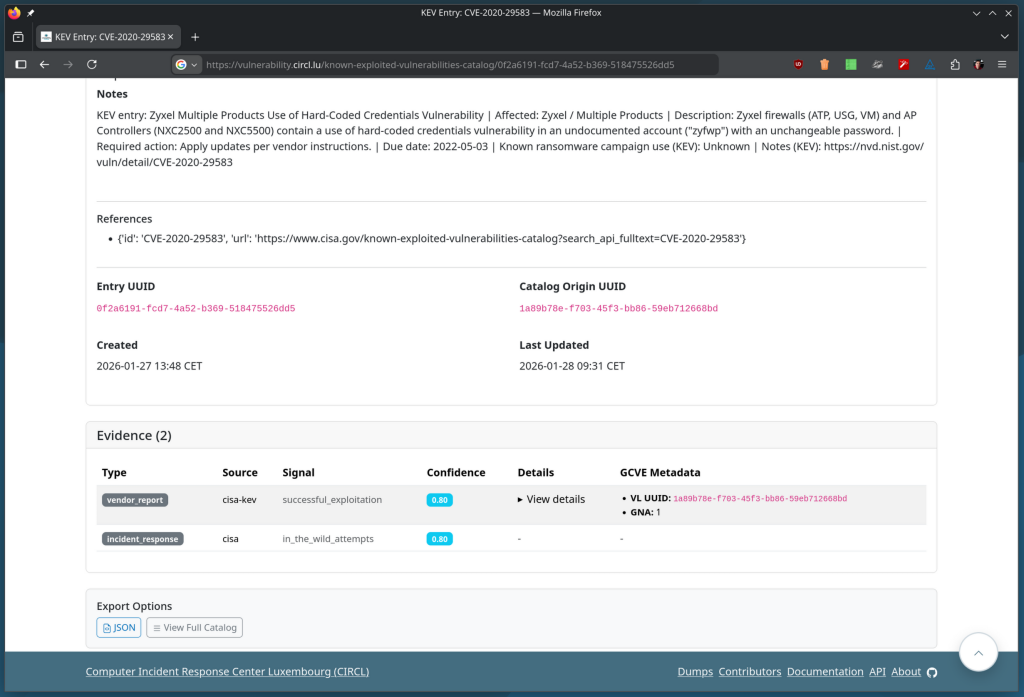
GNU InetUtils Security Advisory: remote authentication by-pass in telnetd

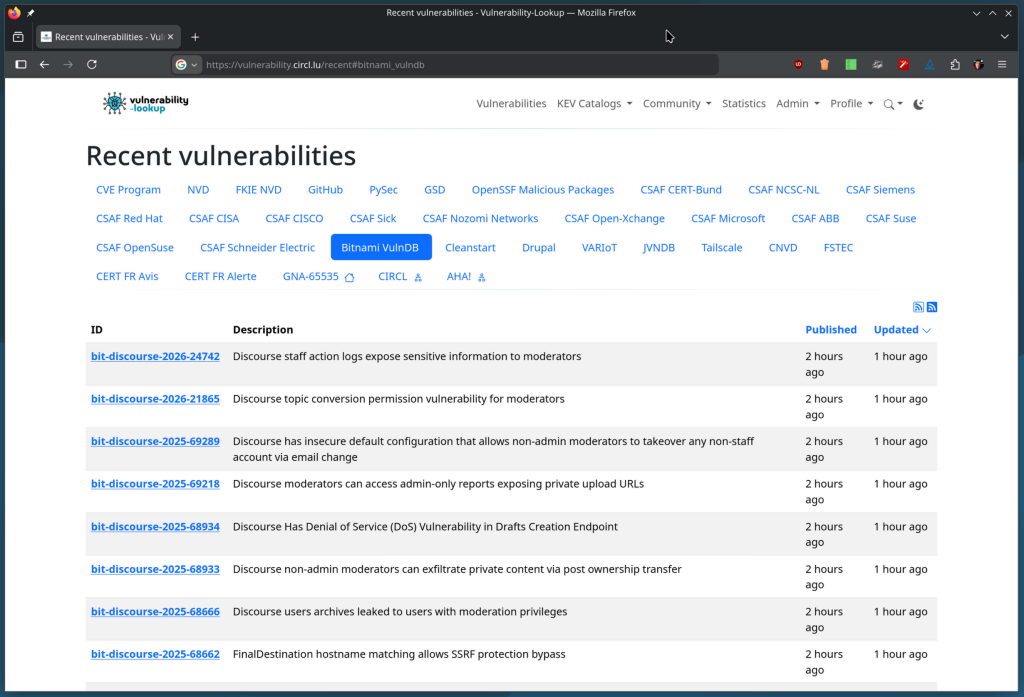
GCVE-1-2026-0007 - Vulnerability-Lookup
Details of the vulnerability GCVE-1-2026-0007 from gna-1 on Vulnerability-Lookup.vulnerability.circl.lu
Dissecting CrashFix: KongTuke's New Toy | Huntress
In January 2026, Huntress Senior Security Operations Analyst Tanner Filip observed threat actors using a malicious browser extension to display a fake security warning, claiming the browser had "stopped abnormally" and prompting users to run a “scan” to remediate the threats. Our analysis revealed this campaign is the work of KongTuke, a threat actor we have been tracking since the beginning of 2025. In this latest operation, we identified several new developments: a malicious browser extension called NexShield that impersonates the legitimate uBlock Origin Lite ad blocker, a new ClickFix variant we have dubbed “CrashFix” that intentionally crashes the browser then baits users into running malicious commands, and ModeloRAT, a previously undocumented Python RAT reserved exclusively for domain-joined hosts.
Dissecting CrashFix: KongTuke's New Toy
Fake ad blocker crashes your browser, then offers a "fix." Go inside KongTuke's CrashFix campaign, from malicious extension to ModeloRAT for VIP targets.Anna Pham (Huntress)
China bans U.S. and Israeli cybersecurity software over security concerns

China bans U.S. and Israeli cybersecurity software over security concerns
China told domestic firms to stop using US and Israeli cybersecurity software, citing national security concerns amid rising tech tensionsPierluigi Paganini (Security Affairs)
Malware peddlers are now hijacking Snap publisher domains
Malware Peddlers Are Now Hijacking Snap Publisher Domains
tl;dr: There’s a relentless campaign by scammers to publish malware in the Canonical Snap Store. Some gets caught by automated filters, but plenty slips through.Alan Pope (https://blog.popey.com/)
New IP leak discovered in Telegram: the built-in proxy exposes your real IP using a single-click flaw!
When you click on a "tg://proxy" link, Telegram starts a connection while ignoring your proxy settings. This exposes your real public IP address, leaking your identity online.
The malicious link appears as a nickname, but will steal your real IP address as soon as the user profile is shown. Android and iOS are both affected. Currently the only solution is using a VPN. Telegram has declared that it will only add a warning popup.
Details: dig.watch/updates/telegram-ip-…
Discovered by: Saurabh
Reported by: 0x6rss and GangExposed RU.
#telegram #security #vulnerability #android #ios #software #opensource #foss #cloud #im #chat #proxy #vpn
One-click vulnerability in Telegram bypasses VPN and proxy protection | Digital Watch Observatory
Researchers say a hidden proxy feature in Telegram can silently expose a user's true network location.jovankr@diplomacy.edu (Digital Watch Observatory)
Is Germany Looking to Put a Backdoor into Arch Linux?
- YouTube
Bekijk je favoriete video's, luister naar de muziek die je leuk vindt, upload originele content en deel alles met vrienden, familie en anderen op YouTube.www.youtube.com